這篇接著上篇從 search_twitter 這個方法開始改寫成 Python
從 API 文件[1]看到只有一個必填欄位 query
回傳是 JSON 格式,
例如:
{
"data": [
{
"id": "1571818370026311682",
"text": "RT @CyberSANEH2020: |Results \ud83c\udf96\ufe0f| #XLSIEM from @AtosES provides #eventmanagement capabilities with advanced prevention and #threat #detectio\u2026"
}
}
我把 code 放在 github 上
https://github.com/stwater20/CTI_Twitter
上一篇我們提到記得先提前安裝 python
我用的版本是 python 3.9
pip3 install requests
pip3 install requests-oauthlib
幾個要注意的點
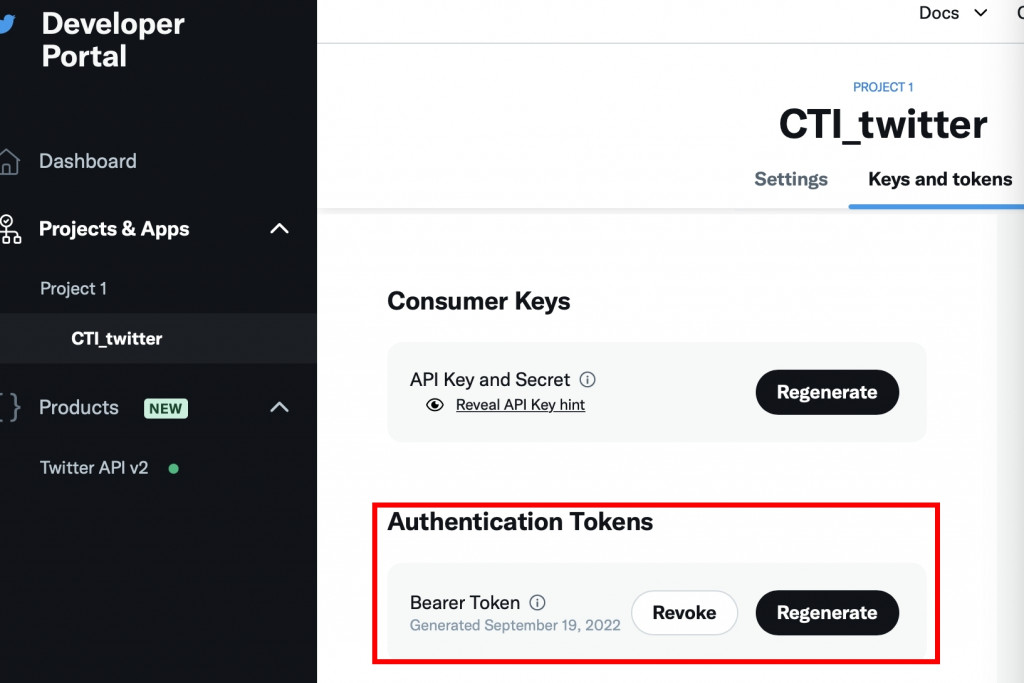
第八行 bearer_token = "填上你的BEARER_TOKEN"
記得替換成你專屬的 token,
忘記的話可以到
https://developer.twitter.com/
重新取得一次
第十二行 放入想要搜尋的關鍵字
search_term = 'threat intelligence'
十八到二十三行是建構 HTTP Request 的 header
def create_headers(bearer_token):
headers = {
"Authorization": "Bearer {}".format(bearer_token),
"User-Agent": "v2SpacesSearchPython"
}
return headers
二十六到三十一行是發出http 請求,如果回傳狀態碼是 200 (正常回應),
則會返回 json 格式回應,如果不是 200 則會跑例外
def connect_to_endpoint(url, headers, params):
response = requests.request("GET", search_url, headers=headers, params=params)
print(response.status_code)
if response.status_code != 200:
raise Exception(response.status_code, response.text)
return response.json()
三十四到三十七行是主程式 main(),
json.dump 是 json 序列化會直接回傳 JSON 格式的字串實例。
def main():
headers = create_headers(bearer_token)
json_response = connect_to_endpoint(search_url, headers, query_params)
print(json.dumps(json_response, indent=4, sort_keys=True))
四十到四十一行指的是以該文件為主要執行時會跑 main()
if __name__ == "__main__":
main()
關於 name 的用途請參考 https://www.geeksforgeeks.org/what-does-the-if-name-main-do/
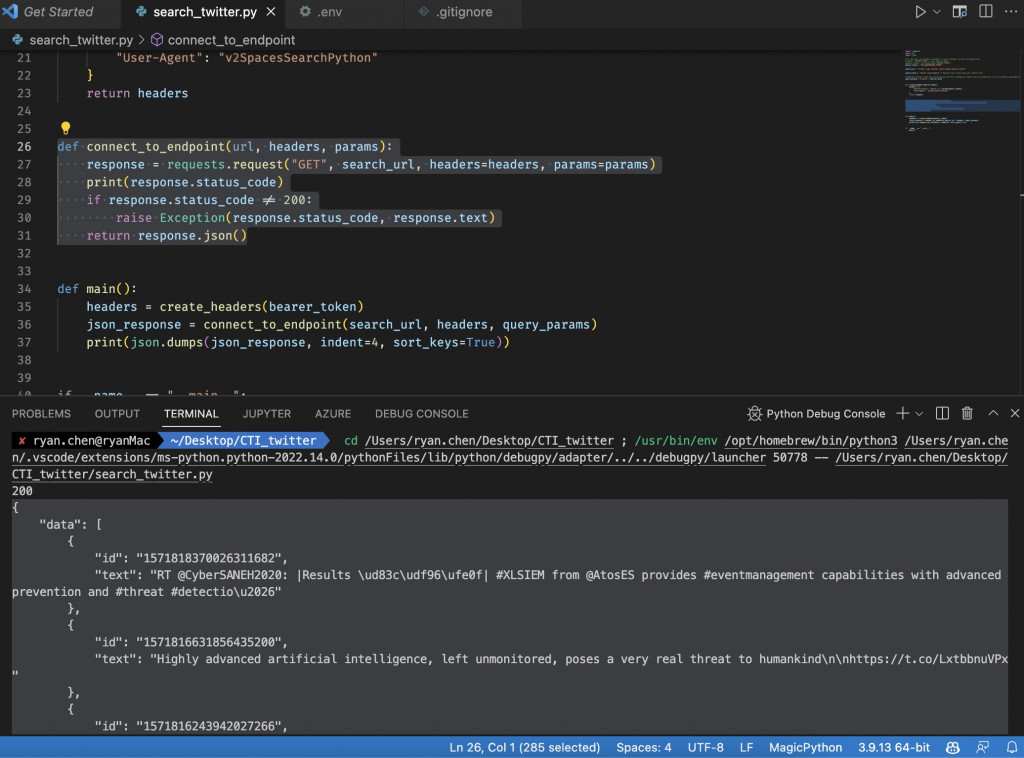
最後執行後,會得到
{
"data": [
{
"id": "1571818370026311682",
"text": "RT @CyberSANEH2020: |Results \ud83c\udf96\ufe0f| #XLSIEM from @AtosES provides #eventmanagement capabilities with advanced prevention and #threat #detectio\u2026"
},
{
"id": "1571816631856435200",
"text": "Highly advanced artificial intelligence, left unmonitored, poses a very real threat to humankind\n\nhttps://t.co/LxtbbnuVPx"
},
{
"id": "1571816243942027266",
"text": "RT @SomaDut96461948: Nevr forget u r investigating a person's mysterious death case whose intelligence is unquestionable\n\nIf Sushant ws con\u2026"
},
{
"id": "1571815273795321857",
"text": "RT @SomaDut96461948: Nevr forget u r investigating a person's mysterious death case whose intelligence is unquestionable\n\nIf Sushant ws con\u2026"
},
{
"id": "1571815268489240577",
"text": "RT @daddyhope: As the election fever gets frenzied, ZANUPF will come together.\n\nAll this counter-intelligence nonsense of big fights has be\u2026"
},
{
"id": "1571808896884293633",
"text": "\ud83d\udcc8 Espa\u00f1a ha sufrido en el segundo trimestre de 2022 una subida del 77% en el n\u00famero de #ciberataques respecto al trimestre anterior, seg\u00fan\u00a0el Observatorio de #Ciberseguridad elaborado por @Exprivia_Italy.\n\n\ud83d\udd17 Puedes consultar el informe completo aqu\u00ed: https://t.co/pce31BZKnA https://t.co/2hFyUSReIu"
},
{
"id": "1571808401247567873",
"text": "@thejackhopkins The comments on this thread are really comical. The threat to this country is not Republicans, its weak minded folks that will believe anything. Our intelligence services run this country, our media and outr internet. Tyranny is coming soon, and you folks are going to let it be"
},
{
"id": "1571807917791391744",
"text": "RT @SomaDut96461948: Nevr forget u r investigating a person's mysterious death case whose intelligence is unquestionable\n\nIf Sushant ws con\u2026"
},
{
"id": "1571807904503836673",
"text": "RT @Balu35001403: Subscribe to the F5 Labs newsletter and get threat intelligence updates from security leaders with decades of experience.\u2026"
},
{
"id": "1571807768881016835",
"text": "RT @SomaDut96461948: Nevr forget u r investigating a person's mysterious death case whose intelligence is unquestionable\n\nIf Sushant ws con\u2026"
}
],
"meta": {
"newest_id": "1571818370026311682",
"next_token": "b26v89c19zqg8o3fpzbk3h4pwslx0xnfch32w1645xjel",
"oldest_id": "1571807768881016835",
"result_count": 10
}
}
明天看看有沒有時間寫一個 OpenCTI 的 connector 來串接我們抓到的資料
